- 12 Posts
- 16 Comments

 2·4 months ago
2·4 months agoI’ve received a lot of reactions on the original post: https://programming.dev/post/10465121
But if someone is involved with the development of Thunderbird I think this is worth reading: https://programming.dev/comment/7677398
For my part I will use the OpenPGP sigin tools for now.
Cheers.

 3·4 months ago
3·4 months agoThank you all for your quick reactions !!
To summarize if I want to use the PDF built-in signing I will need to convert my OpenPGP into a X.509 cert otherwise I can simply use the OpenPGP file signing
I want to stick to the UNIX Philosophy especially:
Write programs that do one thing and do it well.
So I will use the OpenPGP signing tool :)
Thanks !

 1·6 months ago
1·6 months agoThanks for your output, but RSA seem to not be recommended anymore, dig on a search engine…

 1·7 months ago
1·7 months ago@crystal@feddit.de I didn’t know about GrapheneOS too bad it only work Pixel phones (that are also owned by Google ! ) So If I’m against Google for all what they do https://degooglisons-internet.org/en/ I’ll certainly not give them money !
(Finding and importing a phone is something you have to do even when using the stock OS.)
True, but you will do it multiple time if the phone that your looking for doesn’t have an available ROM somewhere…

 2·7 months ago
2·7 months agoIndeed, but in AOSP there is no GMS and that already better !

 3·7 months ago
3·7 months agoHas I found nothing, I’ve write a piece of code in Python 🐍 ! and compile it for Windows…

 3·7 months ago
3·7 months agoThank you @Vilian@lemmy.ca Seem great, I’ll keep it for later :)
But not for what I need now, as
Mutt is a small but very powerful text-based mail client for Unix operating systems
and it’s a “full” client, I need just the SMTP functionality.

 1·7 months ago
1·7 months agoyes, it’s been years that I’m using
CMDand as I’m planning get rid of windows there is no point for me to learn it.
see my comment in the original post ( https://programming.dev/post/6111023) for more info on the suspected bug.

 1·7 months ago
1·7 months agonot yet, I didn’t find enough documentation about that topic.

 11·7 months ago
11·7 months agoIf the computer of the Visitor is already compromised ! your simulation can stop there I think…
My scenario assume that the visitor computer is not compromised.
But let say his traffic get intercepted. Sure a hacker can send his PubKey (2) but in (3) the visitor (should) have already the PubKey of one (or few) verification server. So it should not be possible for an hacker to interfer with the communication (3) right ?

 1·8 months ago
1·8 months ago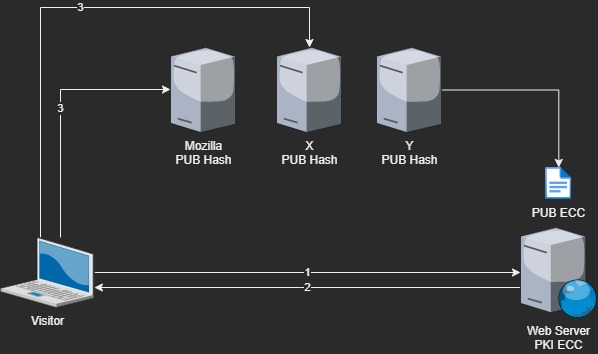
and what about something like this.
- The visitor connect on the website
- he receive the public key
- The key ( it’s hash ) is compared with at least two “verification” server , if they all return a positive match, the visitor can use the pub key to initiate.
The “verification servers” grab the public key directly from the Web server.
Any suggestions, ideas ?

 13·8 months ago
13·8 months agoSo maybe the solution relies trough a blockchain ?
or something that from scratch mind privacy, and decentralization ? Like TOR

 13·8 months ago
13·8 months agoThanks for you reaction @breakingcups@lemmy.world
-
Yes trough Dnssec, or something else ?
-
Maybe we should go toward a blockchain ? but maybe it’s overkill ?
-

 32·9 months ago
32·9 months agoand a True Linux ! not one that has been "infected" with parts that do not respect The Four Essential Freedoms of Free Software
So avoid Ubuntu for example…
have a look a this video https://www.fsf.org/blogs/rms/20140407-geneva-tedx-talk-free-software-free-society/
And for a Linux distrio have a look at https://www.devuan.org 💓
and about windows --> https://itvision.altervista.org/why-windows-10-sucks.html







I’ve gave a longer trial to gpg4win and it’s very power full and easy to use ! Of course it’s pointless to use such a nice tool on a none air-gaped Windows…
For the others there is Gnu-Linux :)